_6: Purdue Level: 3.5
What you're missing in your Purdue Level 3.5 - the iDMZ.
10/6/20242 min read
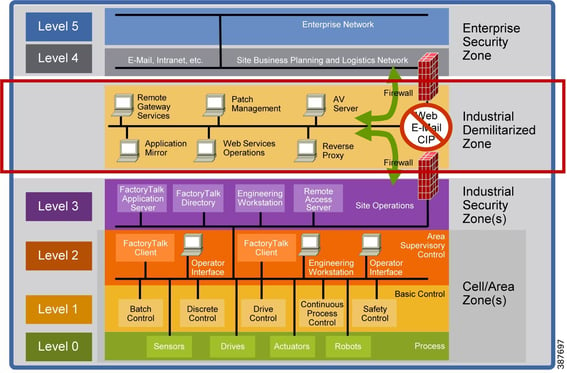
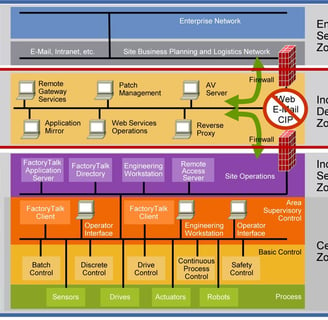
Purdue Level 3.5 is also known as the Industrial Demilitarized Zone (iDMZ). This is the zone that buffers between the OT and the IT security zones. The whole point of the iDMZ is to restrict direct communication between the two security zones, meaning no traffic can transverse the iDMZ, from IT to OT or from OT to IT. The restriction is put in order to protect both zones. Similar to two regions with different political views like North and South Korea, the buffer zone or the DMZ between North and South Korea is used to host communication and negotiation between political leaders. This communication can only be carried out under strict military protocols. Same thing for the iDMZ, there are systems that are set up in the iDMZ to carry out communication between the two zones.
So why is Level 3.5 so important for industrial control systems? This really comes back to the defense-in-depth principle where you have multiple security layers to slow down a breach. The real fact is that YOU, as the end user, have to be prepared that you will eventually get hacked. Having multiple layers of security in place is key to lessen the blow and allow your team to have the time to react.
So is the iDMZ just a single buffer zone between OT and IT? The answer to this is: it really depends. It really depends the services you're providing to users on the business side of things and what services you're using within your OT infrastructure. It also depends on how deep the rabbit how you want to go. In general, the iDMZ should be properly structured to ensure the services are segmented for their different purposes. Please see below for some considerations.
An IDMZ network for jump hosts for remote users.
An iDMZ network for business use like MES/SAP, Historian, CIP Reports for QA, reverse proxy, etc.
An iDMZ network for infrastructure services like DNS, WSUS, Anti-Virus, offsite backup solution, etc.
An iDMZ network for restricted internet services utilizing a web proxy with third party integrated services and monitoring. This should be a separate provider apart from your DNS filtering service if that's something you're using.
So how do you create this iDMZ? One way is to have two firewalls (or four firewalls for a high availability setup). The IT firewall (or a set of IT firewalls) faces the ISP. The OT firewall (or a set of OT firewalls) faces the IT firewalls. Make connections between your IT firewall/s and OT firewall/s. Create logical separation in your OT firewall for the iDMZ and OT. Put in routing and access control lists to control traffic between OT, iDMZ and traffic to the IT firewall. This is the simplest way to build an iDMZ. Another way is to add a firewall or a set of firewalls in the iDMZ bordering the IT firewall. This is also a great way to set up your security as well since hackers will have to get through two firewalls to get to your critical assets.
Photo Courtesy of Cisco


